Elementum’s agent architecture operates on two complementary levels: individual agent design that provides specialized intelligence within deterministic boundaries, and multi-agent coordination that enables complex workflows across organizational boundaries. This document covers the technical architecture, communication protocols, and integration patterns that enable agents to operate reliably in enterprise environments.
Individual Agent Architecture
Core Agent Components
Each Elementum agent follows a standardized internal architecture that balances AI capabilities with deterministic control structures:
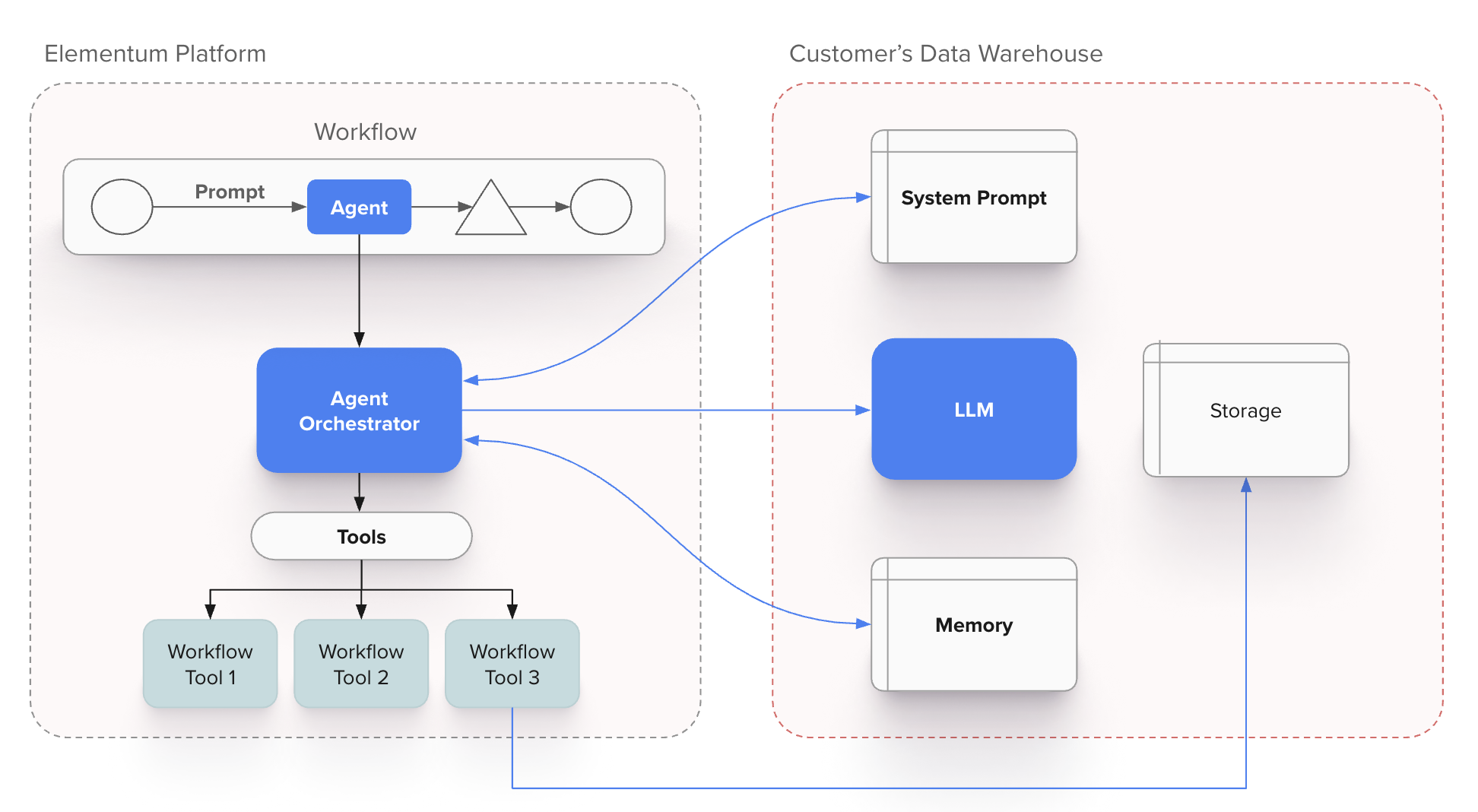
Agent Component Functions
- System Prompts: Define agent behavior, expertise domain, and operational constraints
- Orchestrator: Manages execution flow, tool calls, and contextual state
- LLM Engine: Provides natural language understanding and generation capabilities
- Memory Systems: Maintain context, conversation history, and learned patterns
- Tool Registry: Catalog of functions and integrations the agent can invoke
- Customer Data Access: Secure, governed access to relevant business data
Deterministic Control Mechanisms
The agent orchestrator enforces deterministic behavior through:
- Workflow Action Constraints: Predefined actions that limit agent behavior to approved operations
- Data Access Controls: Strict boundaries around what data the agent can access and modify
- Tool Invocation Rules: Defined conditions for when and how external tools can be used
- Escalation Triggers: Automatic handoff to human oversight based on confidence thresholds or business rules
Multi-Agent Coordination via A2A Protocol
Agent2Agent (A2A) Protocol Implementation
The A2A protocol enables standardized communication between Elementum agents and external agent systems. The protocol operates through several key mechanisms:
Agent Discovery and Registration
Agent Card Structure
Each agent publishes a standardized Agent Card that serves as both a discovery mechanism and capability contract. The Agent Card includes:
- Identity and Capabilities: Unique agent identifier and list of specific functions the agent can perform, such as document analysis, compliance checking, or data transformation.
- Communication Endpoints: Technical connection details including A2A protocol endpoints and health check URLs for establishing secure communication channels.
- Authentication Requirements: Security specifications covering authentication methods, required permissions, and access scopes needed for interaction.
- Data Schemas: Structured definitions of expected input formats and guaranteed output formats to ensure compatible data exchange between agents.
- Governance Metadata: Compliance and operational requirements including audit trails, data residency constraints, and regulatory certifications that govern agent interactions.
A2A Authentication
Elementum supports two authentication methods for A2A communication:
OAuth Client Credentials Flow
Standard OAuth 2.0 client credentials grant for machine-to-machine authentication. External agents obtain access tokens from an authorization server and include them in A2A requests.
Self-Signed JWT Authentication
For scenarios where external agents issue their own JWTs, Elementum validates tokens using the following configuration:
| Field | Description |
|---|
| Header Name | The HTTP header containing the JWT token (typically Authorization) |
| Email Address Claim Name | The JWT claim containing the user identifier (e.g., sub, email). When configured, the agent runs with the permissions of the identified user. |
| JWKS URL | URL to the JSON Web Key Set endpoint for public key retrieval and token verification |
| PEM Key | Alternative to JWKS—paste the plaintext public key directly for JWT verification |
| Field | Description |
|---|
| Claim Name | The JWT claim to validate (e.g., client_id, aud, tenant) |
| Acceptable Values | Comma-separated list of values that satisfy the claim requirement |
Use required claims to scope A2A access—for example, require client_id to match your partner’s registered client identifier, or validate aud contains your agent’s expected audience.
A2A Communication Flow
Inter-Agent Communication Patterns
Synchronous Request-Response
- Direct agent-to-agent calls for immediate responses
- Timeout handling and circuit breaker patterns
- Used for validation, lookup, and simple transformations
Asynchronous Task Delegation
- Long-running operations with callback notifications
- Status polling and progress updates
- Used for analysis, document processing, and complex workflows
Event-Driven Coordination
- Agents subscribe to relevant business events
- Reactive processing based on data changes
- Used for monitoring, alerting, and automated responses
Workflow Integration Architecture
Deterministic Structure Around Non-Deterministic Agents
Agents operate within workflow frameworks that provide governance and predictability:
Workflow-Agent Integration Points
- Task Assignment: Workflow engine determines when and where to invoke agents
- Context Provision: Agents receive structured context and constraints from workflow state
- Result Validation: Agent outputs are validated against business rules before proceeding
- Exception Handling: Failed or low-confidence agent responses trigger defined escalation paths
Summary
Elementum’s agent architecture delivers enterprise-grade automation through a layered approach that balances AI capabilities with deterministic control. Individual agents operate within clearly defined boundaries enforced by orchestrators and workflow engines, while the A2A protocol enables seamless coordination across organizational boundaries without compromising security or governance.
This architecture addresses the fundamental challenge of building reliable systems around probabilistic AI by embedding agents within structured workflows that provide predictable business outcomes. The combination of standardized agent components, robust inter-agent communication protocols, and comprehensive governance controls enables organizations to deploy AI-powered automation at scale while maintaining the compliance, security, and reliability requirements essential for enterprise operations. 